[vc_row][vc_column][vc_column_text]
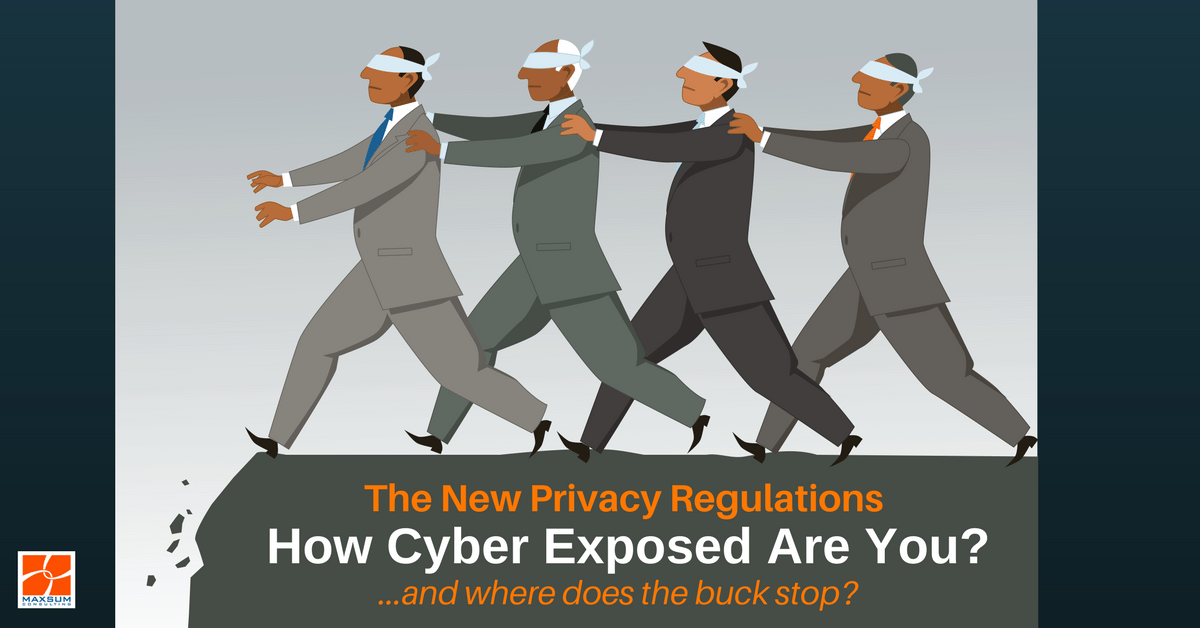
New privacy regulations for cybersecurity – Do you know where the buck stops?
As you get on with the day-to-day grind of running of your business, you probably don’t give too much thought to what IT policy makers are doing in Canberra are doing, much less globally. But the recent surge in cyber-related crime targeting and disabling businesses around the globe has shown legislators that top-down privacy and protection oversight is a non-negotiable. After all a cyberattack costs Australian small businesses an average $6,600 PER ATTACK with that number rocketing up into the tens and hundreds of thousands very quickly the bigger the business and the more invasive the incident. Even more telling, 31% of businesses predict their business would not be able to survive beyond a week if disabled by cyberattack, and statistics indicate that 60% of small businesses who experience a significant cyber breach go out of business within the following 6 months!

In the face of this risk, a tide of regulation is sweeping across cybersecurity, and a newly refreshed set of regulations mean three things for Australian business leaders. We’ve translated what these changes mean for SMEs into plain English.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Cybersecurity is a corporate governance issue
What it means:
Under the Corporations Act 2001 (Cth), the Australian Securities and Investment Commission (ASIC) expects Australian companies to address cyber risks as part of their legal and compliance obligations. Directors are no longer able to push the responsibility of cyber compliance on to the IT Department or service provider. Boards and their directors have the ultimate responsibility to work with managers to analyse the value of the information held by the business, where it sits and how it is protected. This necessitates regular reviews of processes and IT systems and the identification and monitoring of risks, as well as formal forward planning of how the business would be handle cyberattacks and data breaches not only in IT, but across the operations, financial, legal and communications arms of the business.
In plain English:
Trusting that your “IT guy” will have it covered is definitely a recipe for disaster, and having your IT Department or CIO “brief” the board annually will not cut it either. Cybersecurity measures and planning needs to be undertaken systematically and comprehensively by a party with a permanent seat at the board table.
Mandatory data breach reporting is here!
What it means:
If you’re not already across the big changes for business that came into play on February 22, 2018, then it’s time to find out now ! Previously, government agencies, NFPs and businesses with revenue greater than $3 million had a responsibility to take reasonable steps to protect personal information (along with small businesses under the $3m mark that collect, buy or sell personal or health information) under the Privacy Act 1988 (Cth), but now that the Notifiable Data Breaches Scheme has come into force, these entities are now required to investigate suspected data breaches and must now notify of an eligible data breach, with penalties for failure to do so up to $1.8 million for businesses. This change necessitates businesses formulating a Data Breach Response Plan to ensure they have the processes and people in place to investigate and address data breach related issues lawfully within the required timeframe.
In plain English:
Data breaches are not just an “IT issue” but affect the business, the brand and its valuable assets. Businesses will need help to meet new compliance and privacy obligations, to assist employees to understand and apply internal and external policies about information and data handling, and to systemize how data breaches are identified and addressed by formulating a Data Breach Response Plan.
Cybersecurity disclosure may be required
What it means:
ASIC has identified that businesses should consider whether information on their cyber risk should be disclosed to investors when they issue a prospectus, annual directors’ reports or market-sensitive information.
In plain English:
Business will have to make information about their cyber risk publicly available to reassure investors and stakeholders that the board is across cybersecurity issues. Going forward, cybersecurity risks, as well as building and maintaining stakeholder trust, should be prime considerations consistently addressed in public reports and communications.
Do questions about your business’s cyber exposure…and the potential liability … already keep you awake at night?
“Am I asking the right questions? How do I stop worrying about ‘what if and when’? Are we doing enough? Have we made any decisions? Are we making the right decisions? Does the team know what they’re doing?”
Now is definitely the time to find some strategic answers.
If you, your board or executives are asking any of these questions, you’re probably not ready to comply with regulatory changes, much less be fully prepared to weather a serious cyber event. But hopefully, the regulatory changes being made will bring into clearer focus that active oversight of cyber security by boards and the C-suite is no longer just best practice – it is a necessity that will involve both technical and human elements.
Building your business into a cyber mature and cyber resilient organization will be a journey. It will take time, process, follow-through and buy-in across all levels of the organization. And require a team of drivers with business technology expertise that have a permanent seat at your table.[/vc_column_text][/vc_column][/vc_row][vc_row header_style=”qodef-light-header” css=”.vc_custom_1515546160550{margin-top: 40px !important;margin-bottom: 40px !important;padding-top: 35px !important;padding-bottom: 35px !important;background-color: #dddddd !important;}”][vc_column width=”1/4″][vc_single_image image=”1232″ add_caption=”yes” alignment=”center” style=”vc_box_circle”][/vc_column][vc_column width=”3/4″][vc_column_text]
How we can help?
We provide a consulting-led approach to your business technology strategy – making sure you’ve got the right resources in the right places. If you need advice now on your cyber-risk exposure and oversight, call us today on 1300 MAXSUM or shoot us a message on info@maxsum.com.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text] [/vc_column_text][/vc_column][/vc_row]
[/vc_column_text][/vc_column][/vc_row]